Complete Penetration Testing and Ethical hacking Bootcamp
Get started from scratch and become job ready penetration Tester. Be an Ethical Hacker and Hunt as a Bug Bounty Hunters
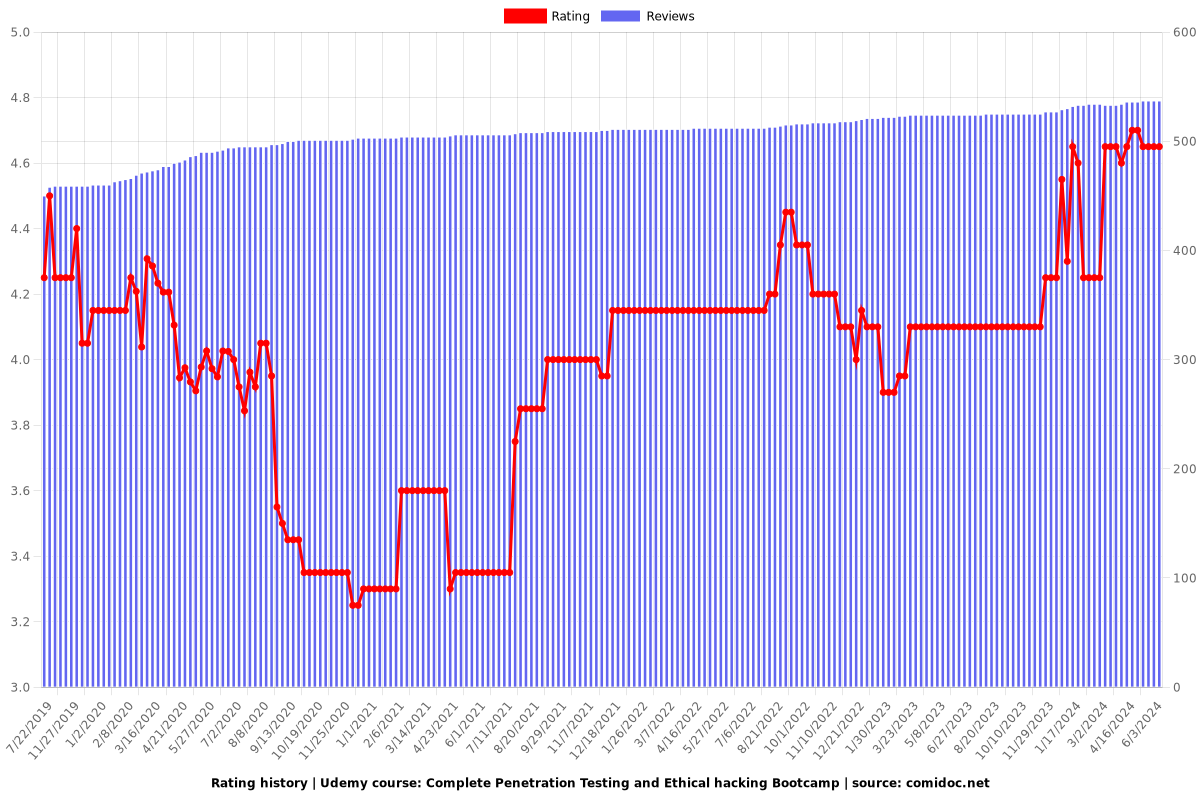
4.65 (537 reviews)

3,697
students
11 hours
content
Jul 2016
last update
$49.99
regular price
What you will learn
By the end you will be able to understand all Information Security terminologies
You will be able to install and use all pentesting tools, even the new ones too
you will be able to hunt bugs and will be able to earn with them by reporting them
you will be able to document the pentesting reports
You will be able to defend your products and network from intrusion by Hackers
Why take this course?
🛡️ **Complete Penetration Testing and Ethical Hacking Bootcamp** 🚀
**Course Headline:** Get started from scratch and become job ready as a penetration tester. Be an Ethical Hacker and Hunt as a Bug Bounty Hunter!
---
📚 **Welcome to the World's Advanced Course on Penetration Testing and Ethical Hacking** 🌐
You're not just another learner; you're someone who chooses to safeguard digital assets from the clutches of hackers. Kudos to your commitment to learning a skill that's in immense demand!
In today's digital age, cyber threats are rampant and headlines often highlight the vulnerabilities of our interconnected world. While many courses focus on creating websites or networking products, this course is dedicated to teaching you how to defend them against attacks. By mastering penetration testing and ethical hacking, you can protect sensitive data and offer your services to businesses big and small, or work independently as a bug bounty hunter.
---
🌍 **Why Learn Penetration Testing and Ethical Hacking?** 🔐
- **Protect Against Attacks:** You'll learn about SQL Injection, XSS attacks, and other vulnerabilities that are often overlooked in standard web development curricula.
- **High Demand Skills:** No official degree is needed; your skills can land you a job in top companies like Google, Apple, and PayPal.
- **Bug Bounties:** Discover how to earn through bug bounty programs, where companies pay for finding and reporting security flaws.
---
🎓 **Course Design for Every Learner** 🛠️
This course is meticulously crafted to be accessible, regardless of your programming background. We've condensed the learning process to focus on practical skills without wasting time on unnecessary prerequisites. Whether you're using Mac, Linux, or Windows, our tools are cross-platform and compatible with all operating systems.
---
👩💻 **What Will You Learn?** 🏫
- Advanced penetration testing techniques and methodologies.
- How to continue learning independently after the course, using free resources and self-study strategies.
- Hands-on experience with custom vulnerable test beds to practice your skills legally and safely.
---
🕵️♂️ **Real-World Challenges Await You** 🚀
We provide you with a safe learning environment using vulnerable test beds, so you can hone your skills without any legal concerns. Plus, our course includes challenges designed to push the boundaries of your capabilities and knowledge.
---
🎯 **Join Our Community of Information Security Professionals** 🌈
This course is your gateway into the fascinating world of Information Security, Penetration Testing, Ethical Hacking, and Bug Bounties. By completing this bootcamp, you'll not only gain practical skills but also join a community of professionals dedicated to protecting our digital landscape.
---
📝 **Important Note:**
While we use Windows XP in a few lectures, it's important to note that Microsoft has dropped support for this operating system. You can either skip those lectures or watch them, as the underlying concepts remain relevant and applicable across modern systems.
---
Ready to embark on your journey to becoming a job-ready penetration tester and ethical hacker? 🛡️ **Enroll in the Complete Penetration Testing and Ethical Hacking Bootcamp today** and take the first step towards an exciting and rewarding career!
Screenshots
Our review
📚 **Course Overview:**
The course in question offers a comprehensive introduction to Penetration Testing, with a significant focus on the use of Kali Linux and its tools. The instruction is largely tutorial-based, providing a solid foundation for those new to IT security. The course content is delivered through a series of lectures that are informative but may require students to seek additional resources to stay current with rapidly evolving technologies in the field.
**Pros:**
- **Instructor Knowledge**: The instructor is well-versed in IT security and provides valuable insights throughout the course. They are known for their knowledge, ability to explain concepts, and incorporating humor into their teaching, making the learning experience more enjoyable and engaging.
- **Resource References**: The course offers numerous references to additional free and paid learning materials, which is a great way to encourage further study beyond the course itself. This approach helps students to continue learning after the course has concluded.
- **Foundational Skills**: Students report that the course has given them enough skills to get started with penetration testing, assuming they have some prior knowledge of security concepts.
- **Practical Approach**: The course is practical and builds a good foundation on how to gather information on a target using tools from the Linux side, which is appreciated by students.
- **Motivational Content**: The content provided, including movies and examples, is challenging and keeps learners motivated throughout the course.
**Cons:**
- **Responsiveness of Instructors**: There have been instances where instructors are not very responsive to student queries, which can be a point of frustration for learners seeking assistance.
- **Course Updates**: Some parts of the course need updating due to recent changes in technology, and it is often suggested that students seek additional sources of information to complement what is taught in the lectures.
- **Relevance of Content**: The course content is from 2016, making some of it outdated and irrelevant, particularly with new programs and security updates. This could lead to learners having to spend extra time on self-directed learning to keep up with current practices.
- **Pacing and Coverage**: While the course is thorough, some students find the pace too brief for their liking or feel that certain topics, such as WiFi security examples, are not adequately covered.
- **Learning Experience**: The background music can be annoying for some students, and the overall teaching style may not suit all types of learners, with one student expressing a strong negative reaction to the author's course.
**General Student Feedback:**
The general sentiment among students is that the course is valuable for beginners and those who already have knowledge of IT security concepts. The practical nature of the course is highly regarded, as are the additional resources provided for further learning. However, some students point out the need for the course to be updated regularly to stay current with the latest in Penetration Testing technology.
**Conclusion:**
Overall, the course offers a solid foundation and introduction to Penetration Testing with Kali Linux, delivered by knowledgeable instructors who provide a wealth of resources for further study. While some students feel the need for more up-to-date content and better responsiveness from instructors, many learners find the course beneficial and engaging. It is recommended that the course be updated to reflect current technology and practices to enhance the learning experience for new students.
Charts
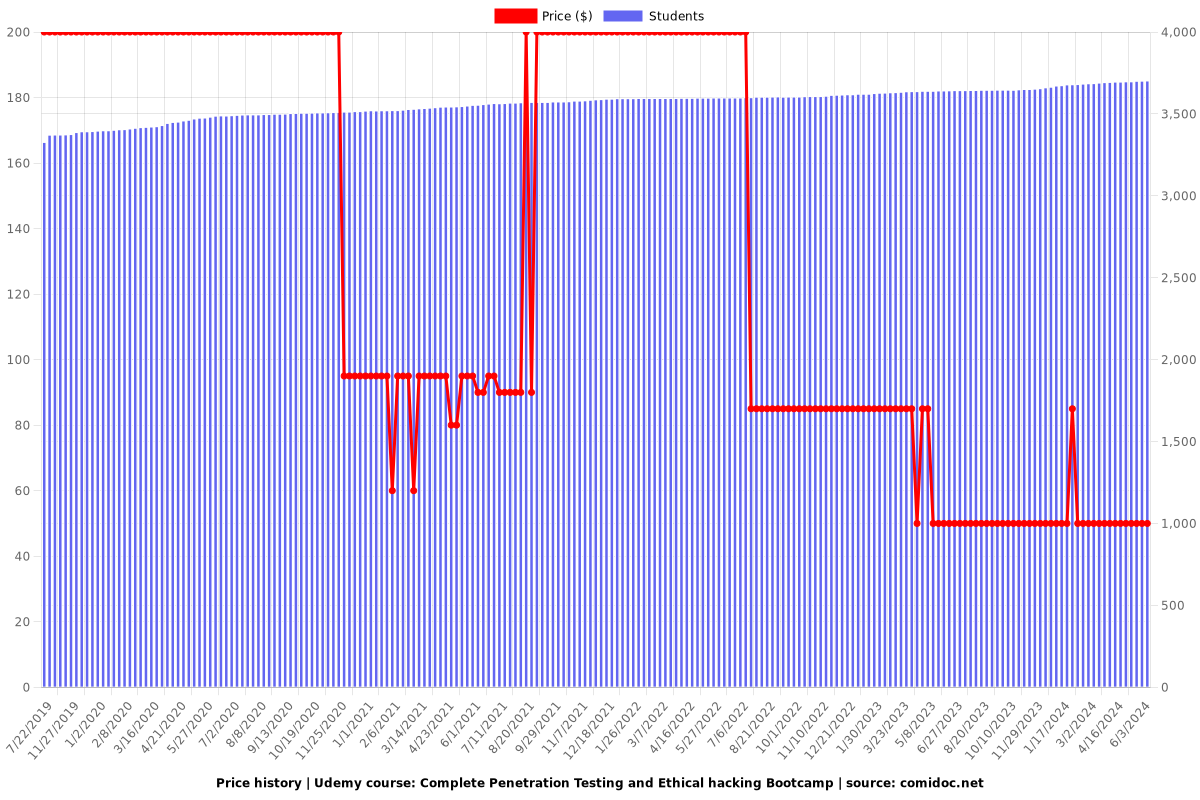
Price
Rating
Enrollment distribution
Related Topics
794544
udemy ID
3/16/2016
course created date
7/22/2019
course indexed date
Bot
course submited by