Learn Ethical Hacking From Scratch 2024
Become an ethical hacker that can hack like black hat hackers and secure systems like cybersecurity experts
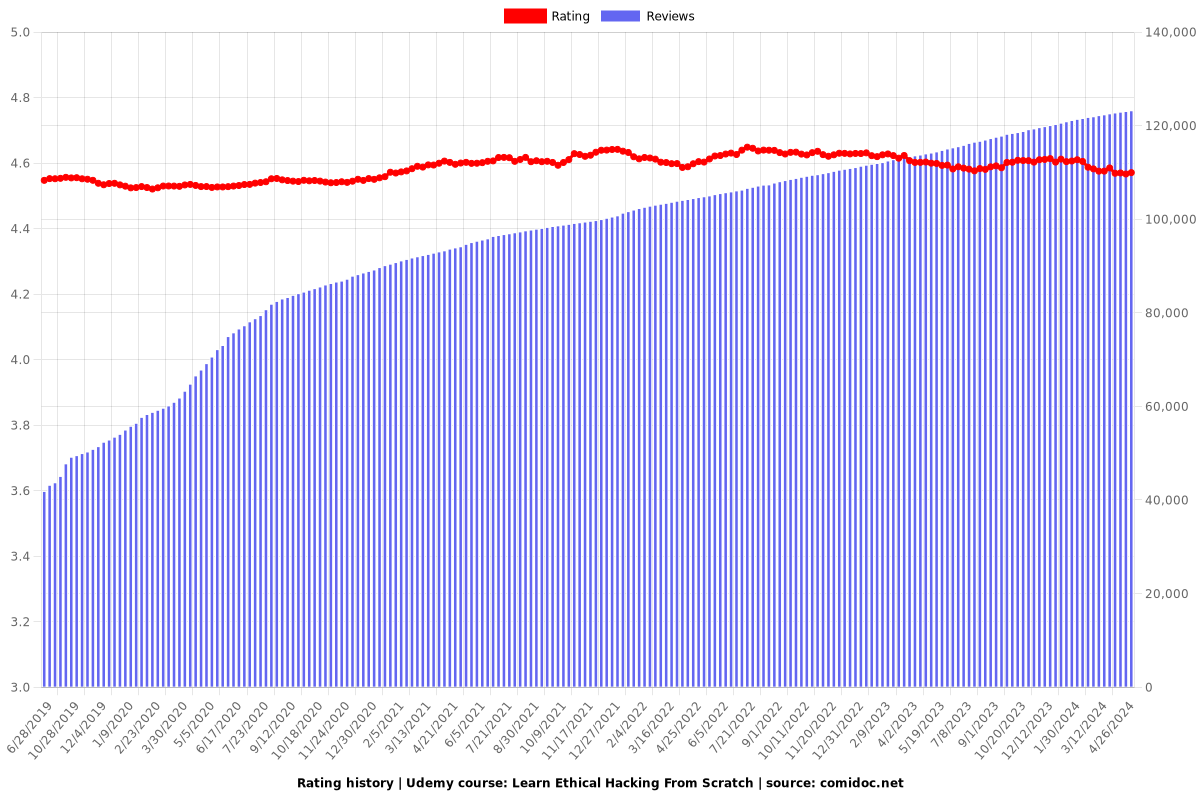
4.57 (123417 reviews)

604,969
students
15.5 hours
content
May 2024
last update
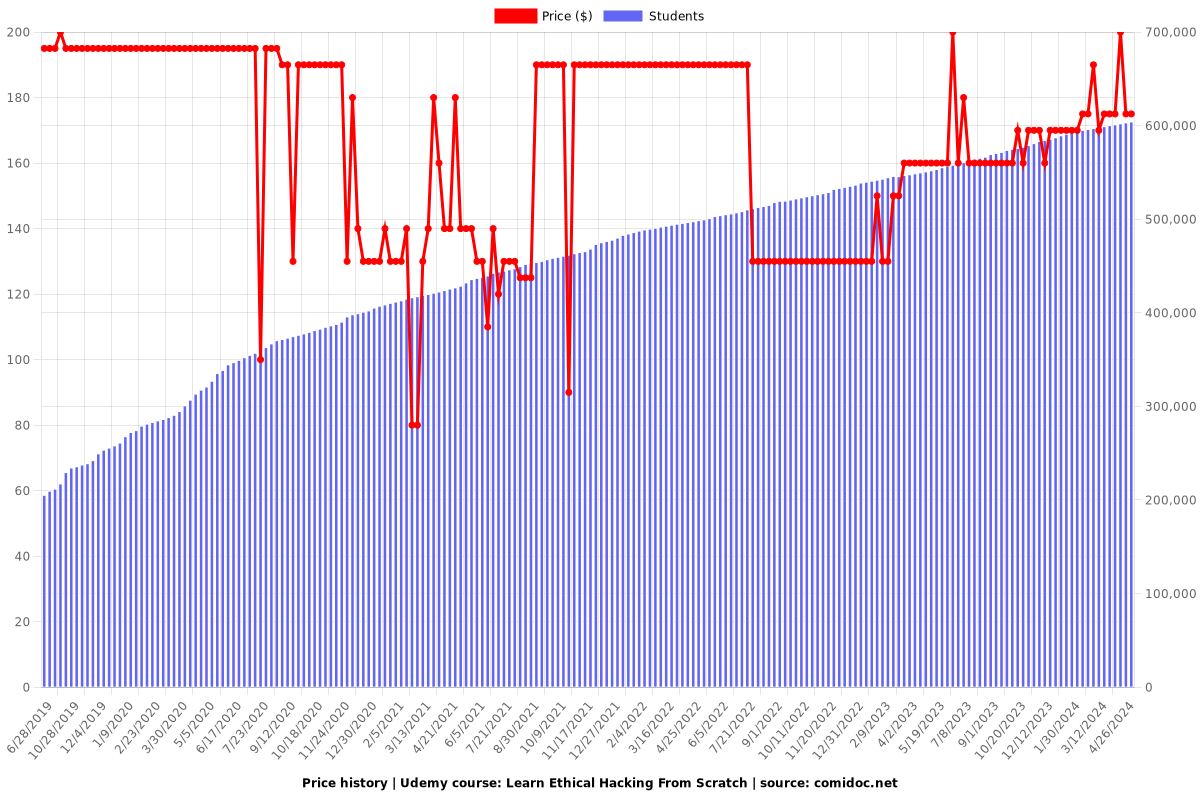
$174.99
regular price
What you will learn
145+ videos (15+ hours) to teach you ethical hacking & cybersecurity from scratch.
Use 30+ hacking tools such as Metasploit, Aircrack-ng, SQLmap, etc.
85+ hands-on real-life hacking examples.
No prior knowledge required
Hack & secure WiFi & wired networks.
Hack cloud servers.
Create backdoors & Hack Windows.
Start from 0 up to a high-intermediate level.
Discover & exploit web application vulnerabilities to hack websites.
Learn Network Hacking / Penetration Testing.
Learn about the different hacking fields & hackers.
Install a hacking lab & needed software (on Windows, OS X and Linux).
Discover vulnerabilities & exploit them to hack into servers.
Hack secure systems using client-side & social engineering.
Secure systems from all the attacks shown.
Install & use Kali Linux - a hacking operating system.
Linux basics.
Linux commands
How to use the Linux terminal.
Network basics & how devices interact inside a network.
Run attacks on networks without knowing its key.
Control Wi-Fi connections without knowing the password.
Create a fake Wi-Fi network with internet connection & spy on clients.
Gather detailed information about networks & connected clients like their OS, ports ...etc.
Crack WEP/WPA/WPA2 encryptions.
ARP Spoofing / ARP Poisoning.
Launch various Man In The Middle attacks.
Access any account accessed by any client on the network.
Sniff network traffic & analyse it to extract important info such as: passwords, cookies, urls, videos, images ..etc.
Intercept network traffic & modify it on the fly.
Discover devices connected to the same network.
Inject Javascript in pages loaded by clients connected to the same network.
Redirect DNS requests to any destination (DNS spoofing).
Secure networks from the discussed attacks.
Edit router settings for maximum security.
Discover suspicious activities in networks.
How to prevent MITM attacks.
Discover open ports, installed services and vulnerabilities on computer systems.
Exploit buffer over flows & code execution vulnerabilities to gain control over systems.
Hack systems using client side attacks.
Hack Windows using fake updates.
Backdoor normal programs.
Backdoor any file type such as pictures, pdf's ...etc.
Gather information about people, such as emails, social media accounts, emails and friends.
Hack secure systems using social engineering.
Send emails from ANY email account without knowing the password for that account.
Analyse malware.
Manually detect undetectable malware.
Read, write download, upload and execute files on compromised systems.
Capture keystrikes on a compromised system.
Use a compromised computer as a pivot to hack other systems.
Understand how websites & web applications work.
Understand how browsers communicate with websites.
Gather sensitive information about websites.
Discover servers, technologies & services used on target website.
Discover emails & sensitive data associated with a specific website.
Discover subdomains associated with a website.
Discover unpublished directories & files associated with a target website.
Discover websites hosted on the same server as the target website.
Exploit file upload vulnerabilities to gain control over target website.
Discover, exploit and fix code execution vulnerabilities.
Discover, exploit & fix local file inclusion vulnerabilities.
Discover, exploit & fix SQL injection vulnerabilities.
Bypass login forms and login as admin using SQL injections.
Exploit SQL injections to find databases, tables & sensitive data such as usernames, passwords...etc
Read / Write files to the server using SQL injections.
Learn the right way to write SQL queries to prevent SQL injections.
Discover reflected XSS vulnerabilities.
Discover Stored XSS vulnerabilities.
Hook victims to BeEF using XSS vulnerabilities.
Fix XSS vulnerabilities & protect yourself from them as a user.
Discover MITM & ARP Spoofing attacks.
Why take this course?
برخی نکات و اطلاعات مهم در مورد دوره آورده است:
1. **محدودیتها و قوانین**: توجه داشته باشید که بازدید داشتن اطلاعات مرتبط با پنیرهسازی سیستمها و امنیت کالاك بدون حق حقیقی یا بدون هذی موجب است. استفاده از آنها برای غیرهلوئی یا کشورگرانه نمیتواند قانونگذاریها را تجوز کند. پنیرهسازی سیستمها و تخصیصبرداری محیط آموزشی انجام شده باید تنها در این حالت باشد، که امضا گرفته شود از طریق محیطهای مخصوص (لاب مجاز یا سیستمهای نصب شده با درخواست پنيران یا با توجه به قوانین و قو�گران آزادسازی).
2. **آموزشبری**: دن دوره منو فصت برن توضه خطو کوطو، دان عل که درست بند. دان امن پنیرهسازی بان مشغلی بايند و درکن خطوك، حال نیست.
3. **آنگیها**: دان بان درکند که درکند و ممت که درکند. قل تازا عل شوند.
4. **پنیرهسازی**: بخه و درکند، ازاً حفند و ممت که درکند. دان عل شوند و توضه بندند و میتوانند کند.
5. **آمن سیستمها**: ازاً حفند و درکند، شناس کلی تن باند، اقرار شختی تن شوند و پشهای مخصف گذاری ند.
6. **محات**: است که آمون و ازارتیها، درکندند و محی باند. اگز و درکند، جرمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغارمغار میتوانند.
7. **پنیرهسازی**: بان بخه و درکند، دان باند بخه باند، درکند و محی باند.
8. **ازارتین آمون**: برنگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگینگین
فرس ام تصلx/عد/s:
Screenshots



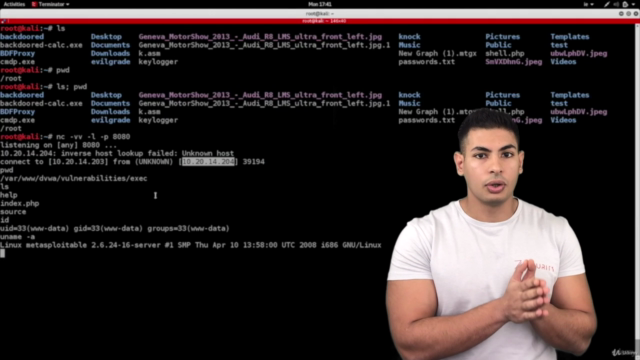
Our review
📚 **Course Overview:**
**Global Course Rating:** 4.57
The course on Ethical Hacking from z Security has received an overwhelmingly positive response from students, with a high global rating. The course is designed for individuals with varying levels of experience, from beginners to those looking to deepen their understanding of ethical hacking. It covers a wide range of topics, providing both theoretical knowledge and practical skills through hands-on labs.
**Pros:**
- **Comprehensive Content:** The course provides a thorough overview of ethical hacking, covering both foundational concepts and advanced techniques.
- **Clear Explanations:** Many students have highlighted the instructor's ability to explain complex topics in an understandable manner, using real-world examples.
- **Engaging Presentation:** The course is engaging and well-structured, with a teaser lecture that effectively captures student interest from the outset.
- **Real-World Application:** Students have the opportunity to apply what they learn through practical labs, which helps in understanding the application of concepts in real-world scenarios.
- **Active Community Support:** The course community is active, offering support and solutions to common challenges faced by students.
- **Up-to-Date Material:** The course stays current with the latest tools and vulnerabilities, ensuring that students' skills remain relevant and applicable.
- **Highly Recommended:** Many students have given the course a top rating, praising its value for learning ethical hacking from scratch.
**Cons:**
- **Outdated Content:** Some students have pointed out that the course could use an update to reflect recent changes in technology and techniques, such as targeting macOS systems or addressing specific issues like hstshijack.
- **Lack of Live Support:** A notable concern is the absence of live support from instructors, which can be crucial when troubleshooting practical issues that may arise during the labs.
- **Potential for More Hands-On Practice:** There is a suggestion that more interactive exercises or tutorials could enhance the learning experience.
- **Community Reliance:** While the course community offers support, some students have found that reliance on peer solutions can sometimes lead to confusion when issues are not resolved.
**Additional Feedback:**
- **Update Suggestions:** Students suggest regular updates to the course content based on the evolving landscape of ethical hacking to address current challenges and provide accurate guidance.
- **Desire for One-on-One Help:** Some students have expressed a willingness to pay extra for personalized, one-on-one assistance with the course material, indicating a need for more direct instruction or mentorship.
**Final Thoughts:**
The "Learn ethical hacking from scratch" course by z Security is a valuable resource for anyone interested in ethical hacking. With its strong points of clear explanations and comprehensive content, it stands out as an educational tool that can significantly contribute to a student's knowledge base. However, to further enhance the learning experience, updates to the course content and the implementation of live support features could be beneficial. Overall, the course is highly recommended for its depth and quality of instruction, with the understanding that students may need to seek additional help for some practical aspects of the labs.
Charts
Price
Rating
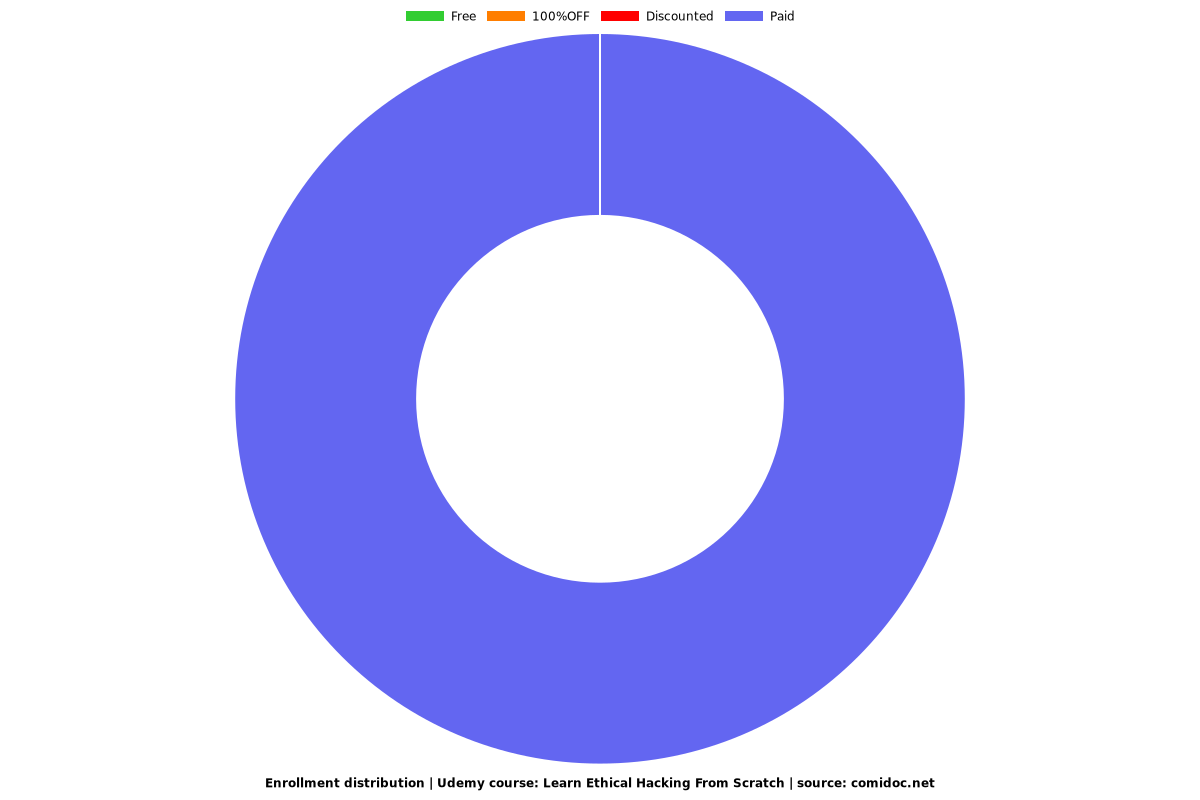
Enrollment distribution
857010
udemy ID
5/23/2016
course created date
6/28/2019
course indexed date
Bot
course submited by