Website Hacking / Penetration Testing
Hack websites & web applications like black hat hackers and secure them like experts.
4.55 (19883 reviews)

125,551
students
10.5 hours
content
May 2024
last update
$159.99
regular price
What you will learn
100+ Videos (10+ hours) to teach you website hacking from scratch.
50+ hands-on real-life website hacking examples - from simple to advanced.
Discover, exploit and mitigate a number of dangerous web vulnerabilities.
Hack cloud servers using these vulnerabilities.
No prior knowledge in Linux, hacking or programming is required.
Advanced post exploitation - pivoting, dump the database, privilege escalation, etc
Bypass security & advanced exploitation of these vulnerabilities.
Bypass security & filters.
Create a hacking lab.
Intercept requests using a proxy.
Adopt SQL queries to discover and exploit SQL injections in secure pages.
Gain full control over cloud servers using SQL injections.
Discover & exploit blind SQL injections.
Install Kali Linux - a penetration testing operating system.
Learn linux commands and how to interact with the terminal.
Learn linux basics.
Understand how websites & web applications work.
Understand how browsers communicate with websites.
Gather sensitive information about websites.
Discover servers, technologies & services used on target website.
Discover emails & sensitive data associated with a specific website.
Find all subdomains associated with a website.
Discover unpublished directories & files associated with a target website.
Find all websites hosted on the same server as the target website.
Discover, exploit and fix file upload vulnerabilities.
Exploit advanced file upload vulnerabilities & gain full control over the target website.
Discover, exploit and fix code execution vulnerabilities.
Exploit advanced code execution vulnerabilities & gain full control over the target website.
Discover, exploit & fix local file inclusion vulnerabilities.
Exploit local file inclusion vulnerabilities to to get a shell.
Exploit advanced local file inclusion vulnerabilities & gain full control over the target website.
Exploit advanced remote file inclusion vulnerabilities & gain full control over the target website.
Discover, fix, and exploit SQL injection vulnerabilities.
Bypass login forms and login as admin using SQL injections.
Writing SQL queries to find databases, tables and sensitive data such as usernames ad passwords using SQL injections
Bypass filtering, and login as admin without password using SQL injections.
Bypass filtering and security measurements.
Read / Write files to the server using SQL injections.
Patch SQL injections quickly.
The right way to write SQL queries to prevent SQL injections.
Discover basic & advanced reflected XSS vulnerabilities.
Discover basic & advanced stored XSS vulnerabilities.
How to use BeEF framwork.
Hook users to BeEF using reflected & XSS vulnerabilities.
Steal credentials from hooked targets.
Run javascript code on hooked targets.
Create Windows backdoors.
Hack computers using XSS vulnerabilities.
Fix XSS vulnerabilities & protect yourself from them as a user.
Brute force & wordlist attacks.
Create a wordlist or a dictionary.
Launch a wordlist attack and guess admin's password.
Discover all of the above vulnerabilities automatically using a web proxy.
Run system commands on the target webserver.
Access the file system (navigate between directories, read/write files).
Download, upload files to / from hacked servers.
Bypass security measurements.
Access all websites on the same webserver.
Connect to the database and execute SQL queries or download the whole database to the local machine.
Discover, exploit and mitigate CSRF vulnerabilities.
Why take this course?
🎉 **Master Website Hacking & Penetration Testing** 👨💻🏫
---
### **Hack Like a Pro, Secure Like an Expert!**
🚀 **Course Headline:** _Hack websites & web applications like black hat hackers and secure them like experts._
---
### **Course Introduction:**
Welcome to my comprehensive course on *Website Hacking / Penetration Testing*! 🌐✨ This is your journey from zero to hero in the world of cybersecurity. **No prior knowledge** required – we'll cover everything you need to know, step by step. By the end of this course, you'll be able to **_hack websites like a black-hat hacker_** and **_secure them like a seasoned security expert!_** 🛡️
---
### **Course Overview:**
This highly **practical** course doesn't just stop at theory. It dives deep into the practical aspects of website penetration, providing you with hands-on experience using a variety of tools. You'll learn through real-world scenarios and labs designed to test your skills effectively. 🔧
---
### **Course Breakdown:**
#### **Section 1: Setting Up Your Lab**
Before we dive into the nitty-gritty, you'll need a safe environment to practice your newfound skills. We'll guide you through setting up your own lab for ethical hacking. 🏭
---
#### **Section 2: Core Vulnerabilities & Exploitation**
This is where the real learning begins! We cover a range of vulnerabilities, including but not limited to:
- Information Disclosure
- File Upload
- Code Execution
- Local File Inclusion (LFI)
- Remote File Inclusion (RFI)
- SQL Injection (SQLi)
- Cross Site Scripting (XSS)
- Insecure Session Management
- Brute Force & Dictionary Attacks
- Client-Side Request Forgery (CSRF)
For each vulnerability, we'll analyze the code causing these issues and understand how to exploit them. 🛠️
---
#### **Section 3: Post Exploitation Techniques**
Once you've gained access, what do you do next? This section will teach you how to navigate a compromised system, execute commands, access databases, and escalate privileges. You'll learn to use tools like Weevely, Metasploit, BeEF, and more to their full potential. 🕵️♂️
---
### **Tools & Technologies:**
You'll get hands-on experience with a suite of powerful tools:
- Kali Linux
- Weevely
- THC-Hydra
- Netcat
- Dev tools (Postman, cURL)
- Burp Suite
- OWASP Zap
- Metasploit
- BeEF (Browser Exploitation Framework)
- Dirb
- Maltego
- Knockpy
---
### **Support & Certification:**
You'll have **24/7 support** to help you navigate through any challenges. And upon completion, you'll receive a Course Completion Certificate from Udemy – a testament to your new skills! 🏆
---
### **Ethical Considerations:**
This course is designed for educational purposes only. All attacks are performed in a controlled environment or with explicit permission. Remember, ethical hacking is about protecting systems, not compromising them. ⚖️
---
### **Join the Community of Cybersecurity Professionals**
Enroll now to join a community of aspiring cybersecurity professionals and experts. Together, we'll explore the depths of web vulnerabilities, learn to protect against them, and contribute to the security of the digital world. 🌍💻
---
### **Ready to Begin Your Cybersecurity Journey?**
Check out the curriculum and course teaser for a sneak peek into what you'll learn. Let's embark on this exciting adventure together! 🚀🔥
---
*Note: This course is a solo effort by Zaid Sabih & zSecurity. It is not affiliated with any other organization or certification exam, except for the Udemy Course Completion Certificate.*
Screenshots

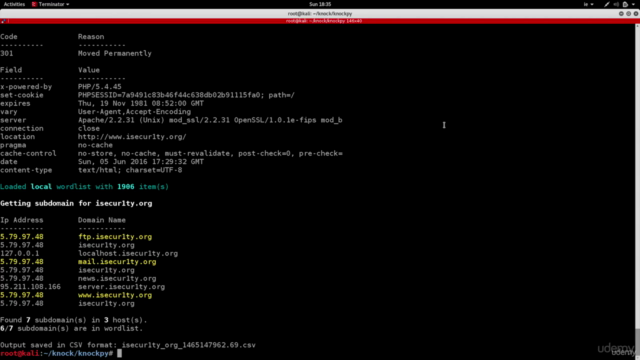

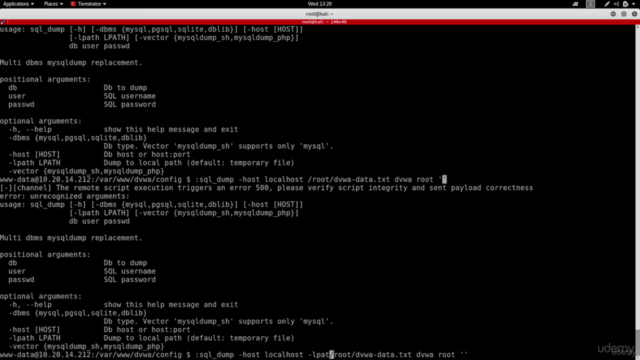
Our review
Based on the feedback you provided, it seems that the course on "Web Security & Hacking" offered by Zaid Al-Khuzaie has received a mix of positive and negative reviews. Here's a summary of the key points from the feedback:
**Positive Feedback:**
1. **Practical Approach:** The course is praised for its practical approach, combining theory with practice, which makes the course understandable and practical.
2. **Teaching Style:** Zaid's teaching style is considered effective, as he uses engaging examples to illustrate concepts.
3. **Introduction to Tools:** Students appreciate being introduced to tools for testing web applications, which they found eye-opening.
4. **Talented and Positive Teacher:** Zaid is described as a talented and positive teacher who makes the course enjoyable.
5. **Material and Examples:** The material provided in the course is well-explained, and the lectures are not just theoretical but also include practical examples.
6. **Real-world Scenarios:** The course covers how to carry out attacks as well as how to mitigate vulnerabilities after they are found.
7. **Completion Experience:** Many students reported that completing the course was a satisfying experience, and they feel better equipped in the pentest world.
**Areas for Improvement:**
1. **Up-to-date Content:** Some students feel that the course content is out of date with the latest developments in the bug bounty world, especially regarding techniques like Server Side Template Injection (SSTI), XXE, and JWT attacks. They suggest updating the material to reflect current practices.
2. **Coverage of Different Technologies:** Students are looking for more comprehensive coverage of databases beyond just the LAMP stack, including MSSQL and Oracle.
3. **Repetition and New Features:** Some feedback indicates there could be less repetition and more new features or content to enhance learning.
4. **Software Information:** The course is criticized for poor software information and lack of detailed explanations, particularly in Java.
5. **Responsiveness to Student Questions:** There are concerns about the timeliness and quality of responses to student questions and problems.
6. **Student Support:** Some students express a desire for better communication and support from the course instructors, suggesting that more attention should be given to addressing student issues promptly.
**Suggestions for Future Content:**
1. **Updates:** Students suggest that the course content should be regularly updated to reflect the latest trends and techniques in web security and hacking.
2. **Bug Bounty Course:** There is a suggestion for a potential bug bounty course similar to "The Web Application Hacker's Handbook" by Dafydd Stuttard.
3. **Certification Beyond the Course:** Some students mention that certification is just the beginning and emphasize the importance of continuing education and practical experience in the field.
Overall, while there are some areas for improvement, particularly in keeping the content current and providing better support to students, the course is generally well-received for its comprehensive coverage of web security and hacking fundamentals, practical examples, and Zaid's teaching style.
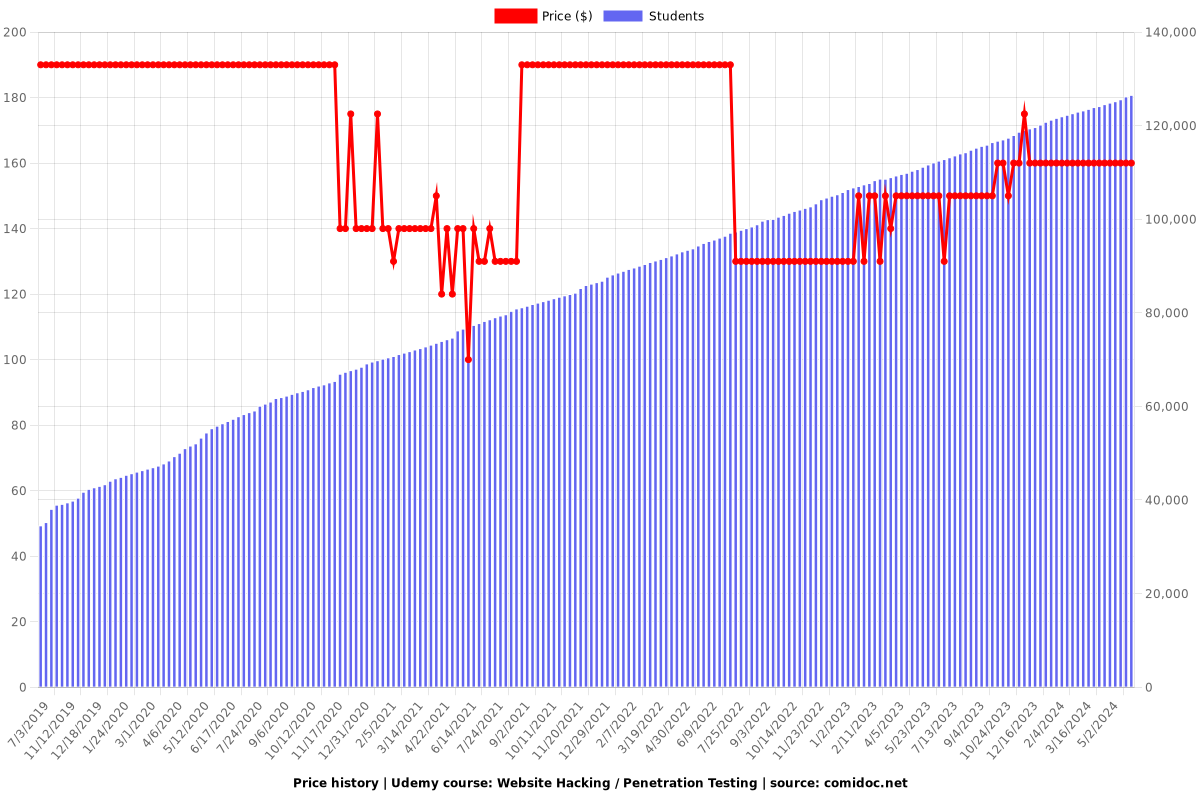
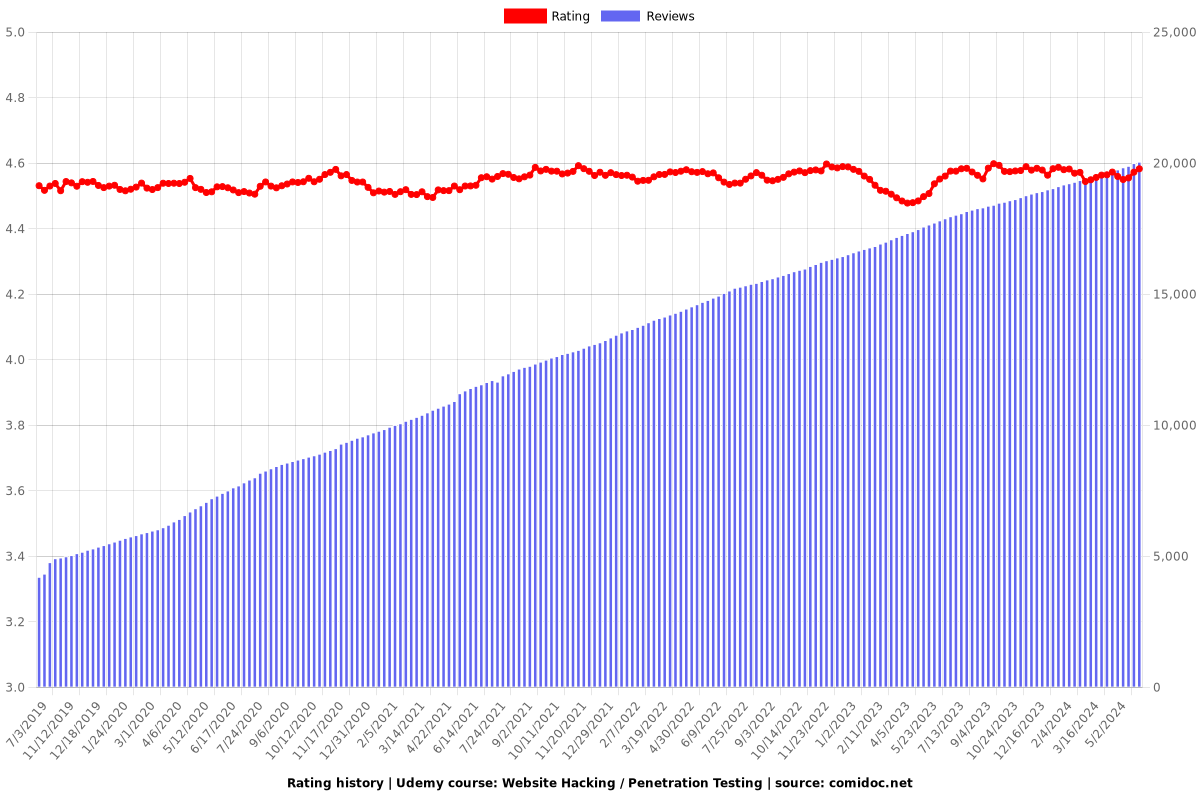
Charts
Price
Rating
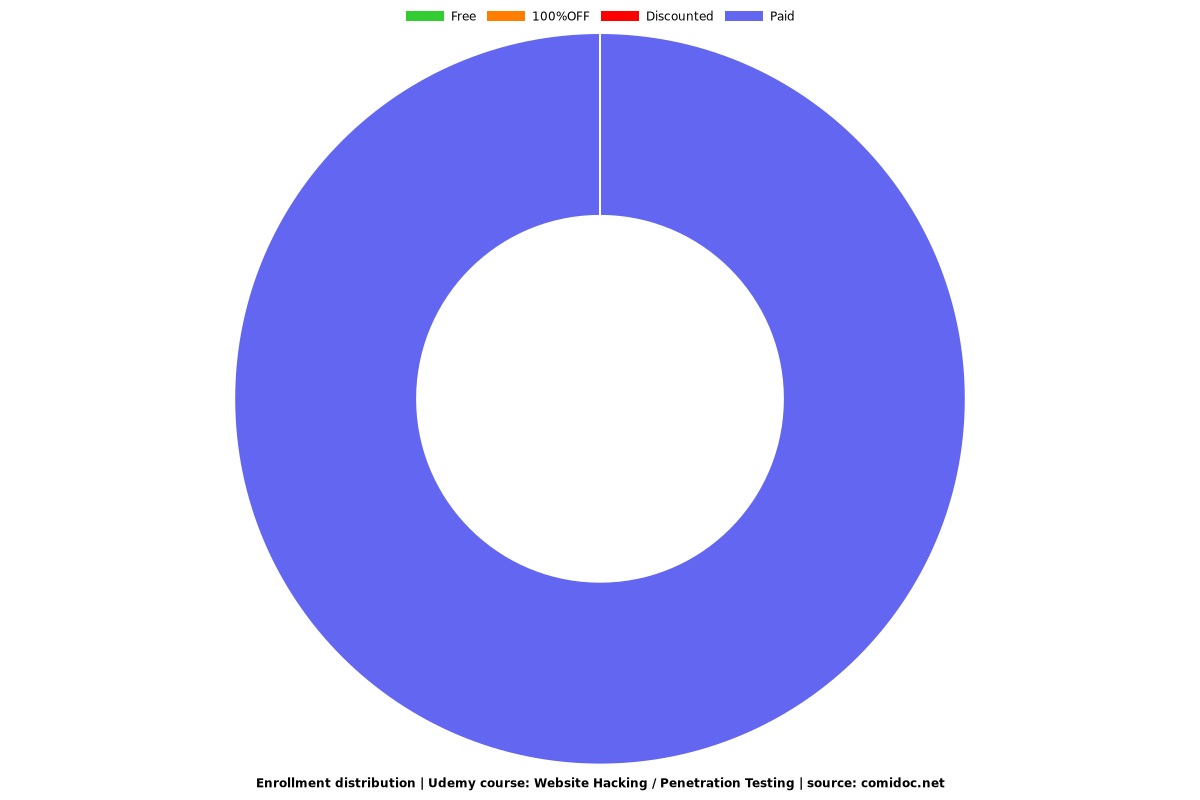
Enrollment distribution
Related Topics
984734
udemy ID
10/15/2016
course created date
7/3/2019
course indexed date
Bot
course submited by