Ethical Hacking: Network Scan Nmap& Nessus| Network Security
Scan networks with vulnerabilities by using Nmap& Nessus. Master Cyber Security, ethical hacking, network hacking skills
4.61 (1570 reviews)

16,426
students
4 hours
content
May 2024
last update
$119.99
regular price
What you will learn
Ethical hacking involves a hacker agreeing with an organization or individual who authorizes the hacker to levy cyber attacks on a system or network.
In addition to proficiency in basic computer skills and use of the command line, ethical hackers must also develop technical skills related to programming.
Ethical hacking is a good career because it is one of the best ways to test a network. An ethical hacker tries to locate vulnerabilities in the network.
Many hackers use the Linux operating system (OS) because Linux is a free and open-source OS that anyone can modify it. It’s easy to access and customize .
Ethical hacking is legal because the hacker has full, expressed permission to test the vulnerabilities of a system. An ethical hacker operates.
The different types of hackers include white hat hackers who are ethical hackers and are authorized to hack systems.
Whether you want to get your first job in IT security, become a white hat hacker, or prepare to check the security of your own home network.
The Certified Ethical Hacker (CEH) certification exam supports and tests the knowledge of auditors, security officers, site administrators
Passing the Certified Information Security Manager (CISM) exam indicates that the credentialed individual is an expert in the governance of information security
Learn how to use Nmap
Learn how to use Nessus
Learn about network scan types
Learn about script scanning
Become ethical hacker
Learn ethical hacking
Learn Ethical Intelligence
Learn about nmap
Learn about nmap nessus
It is expert nmap course
Learn about nmap metaspolit
Complete nmap
Why take this course?
¡Hola! It seems like you've provided a comprehensive overview of ethical hacking, including the legal aspects, various certifications, types of hackers, and the value of staying up-to-date with the latest security practices. Your message highlights the importance of understanding both the offensive and defensive sides of cybersecurity to effectively protect systems and networks against malicious attacks.
Ethical hacking is a critical component of modern cybersecurity strategies. It involves using the same tools and techniques as malicious hackers, but in a legal and authorized manner to identify and fix vulnerabilities before they can be exploited by attackers. This proactive approach is essential for maintaining the integrity, confidentiality, and availability of data and systems.
The CEH (Certified Ethical Hacker) certification and CISM (Certified Information Security Manager) exams are examples of formal recognitions of expertise in ethical hacking and information security management. These certifications demonstrate a professional's commitment to the field and their mastery of key concepts, tools, and techniques.
As for the types of hackers, it's important to understand the distinction between white hat (ethical), black hat (malicious), grey hat (ambivalent), red hat (vigilante), green hat (novice), state-sponsored, hacktivist, whistleblower, script kiddie, and blue hat hackers. Each type plays a role in the cybersecurity landscape, and it's crucial to distinguish between them to effectively address cyber threats.
Your commitment to offering up-to-date content and personal support in your course is commendable. It ensures that learners not only gain knowledge but also have access to ongoing education in a field that is constantly evolving.
Lastly, it's essential to remember that all the skills and knowledge acquired through learning about ethical hacking must be used responsibly and within the boundaries of the law. Ethical hackers are the guardians of cyberspace, helping to keep our digital world safe for everyone.
If you have any more questions or need further clarification on any aspect of ethical hacking or cybersecurity, feel free to ask!
Screenshots



Our review
🏅 **Global Course Rating:** 4.51
**Overview:**
Muharrem AYDIN's course on Network Scanning, Vulnerability Assessment and Ethical Hacking has received an overwhelmingly positive response from learners across the globe. The course is commended for its clarity in explaining complex topics, detailed explanations of tools like nmap and nessus, and the practical approach to learning through examples and demonstrations.
🔹 **Pros:**
- **Expert Instruction:** Muharrem AYDIN is praised for his deep knowledge and clear presentation of advanced security topics.
- **Ease of Understanding:** Complex concepts like OSI Layers are made understandable, which is a testament to the instructor's ability to communicate effectively.
- **Hands-On Learning:** Real-life scenarios and step-by-step examples help learners grasp the practical application of the tools and techniques discussed.
- **Comprehensive Coverage:** The course provides a thorough exploration of network scanning and vulnerability assessment, making it suitable for beginners as well as professionals looking to refresh their skills.
- **Engaging Content:** The course structure is appreciated for being short and to the point, which keeps learners engaged throughout the material.
- **Value for Money:** Many learners consider this course a cost-effective way to enhance their skill set in cybersecurity.
- **Supportive Learning Environment:** The instructor actively responds to Q&A, ensuring that learners are supported throughout the course.
🔹 **Cons:**
- **Technical Difficulties:** Some learners encountered issues with course materials, such as missing files when setting up Kali Linux on a virtual machine, which caused delays in their learning process.
- **Course Structure Improvement:** A few learners suggest that certain sections of the course, particularly sections 6, 7, and 8, could benefit from more practical examples to enhance understanding.
- **Assessment Availability:** There have been instances where questionnaires were not available, and as a result, some learners were unable to receive a certificate upon course completion.
**Learner Testimonials:**
- "He explains well... I could finally understand OSI Layers for example. Detailed nmap explanations are good."
- "Yes, I am very much excited about the course! Even I don't want such kind of obstruction in between the course until the course is finished."
- "I am reviewing many security training courses... This one stands out with its clarity and depth."
- "The nmap information was really insightful and has helped me a lot as a developer."
- "It would be great if we could have PPT or PDF files for referencing the Key Topics as cheatsheets."
**Conclusion:**
Muharrem AYDIN's course is highly recommended for individuals interested in learning about network scanning, vulnerability assessment, and ethical hacking. The positive feedback from learners underscores the effectiveness of the course content and delivery. However, it's important to address the technical issues and potential improvements in certain sections to ensure an optimal learning experience for all students.
Charts
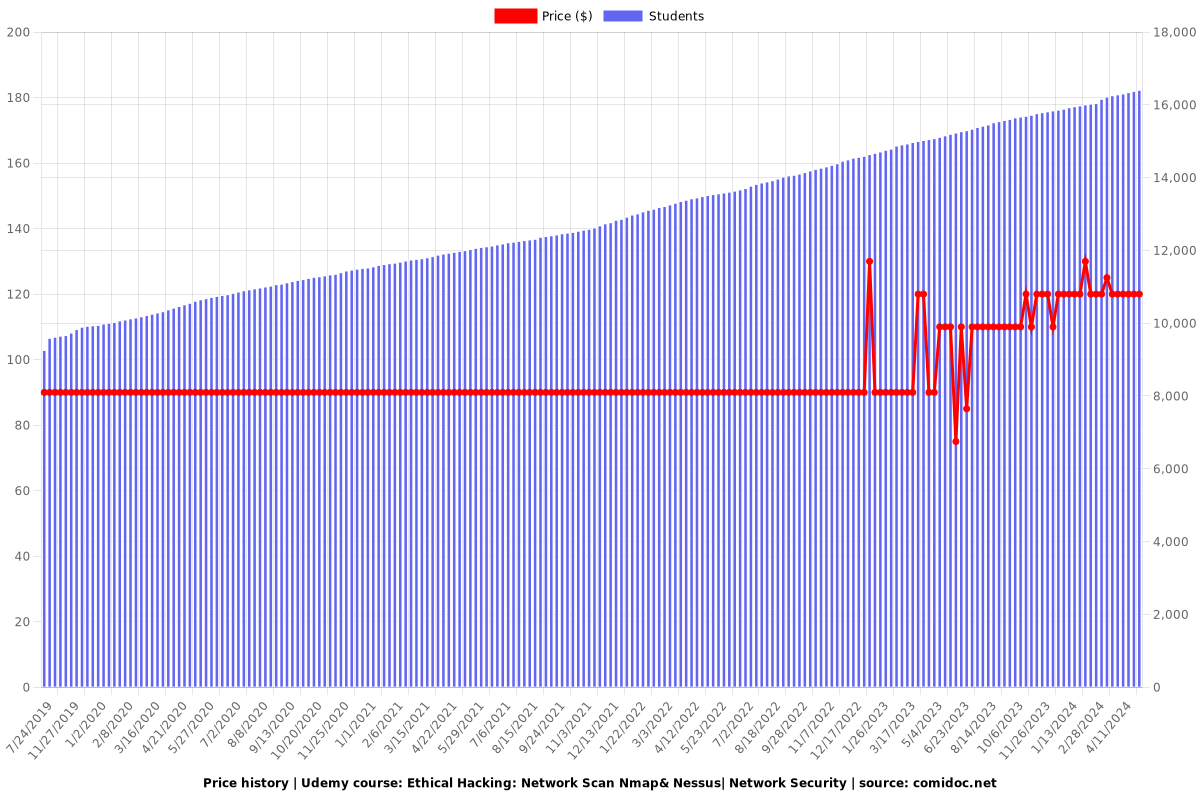
Price
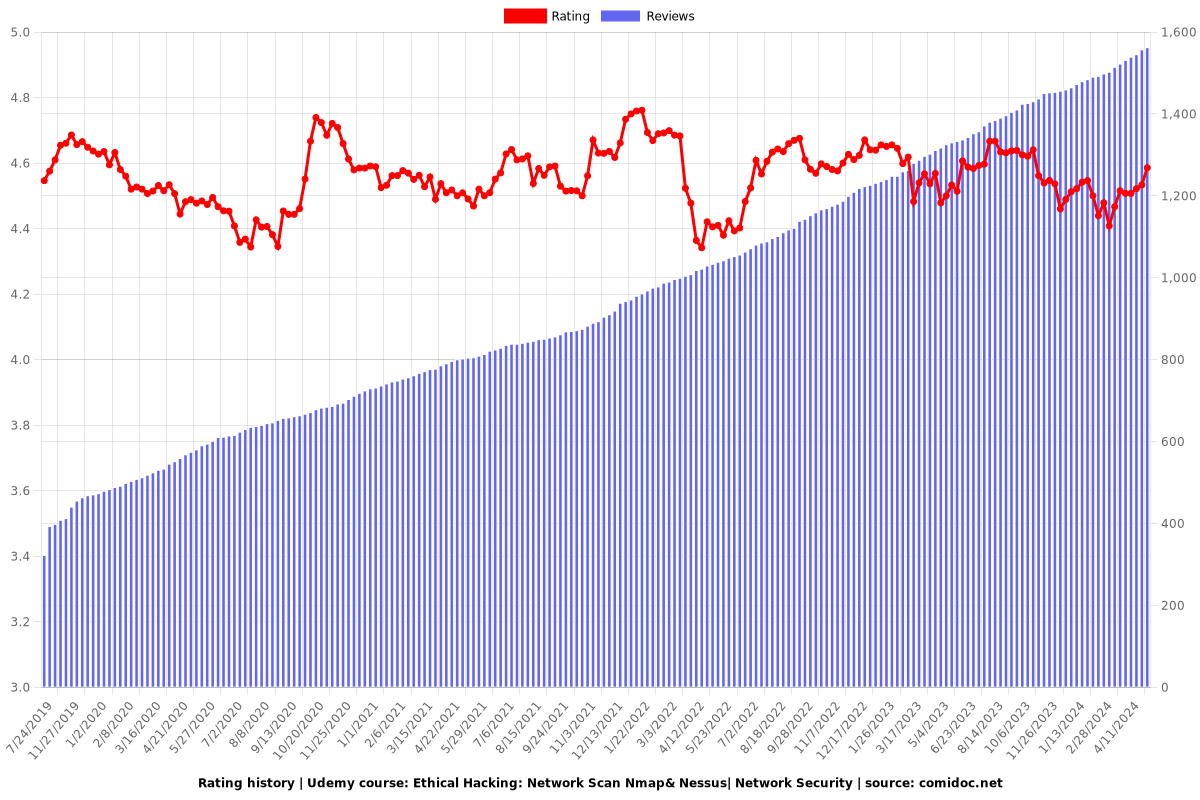
Rating
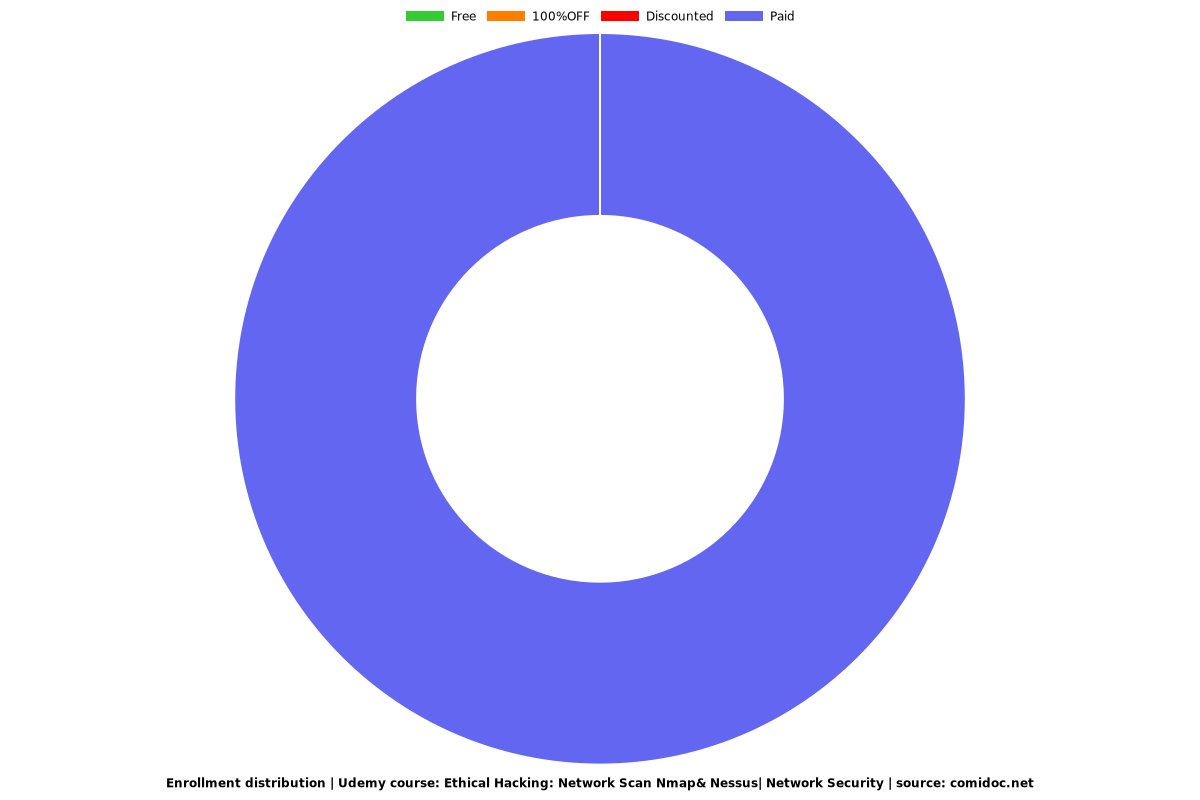
Enrollment distribution
Related Topics
1563128
udemy ID
2/20/2018
course created date
7/24/2019
course indexed date
Bot
course submited by