The Complete Ethical Hacking Bootcamp: Beginner To Advanced!
Learn hands-on ethical hacking, penetration testing, web app pentesting and Python scripting.
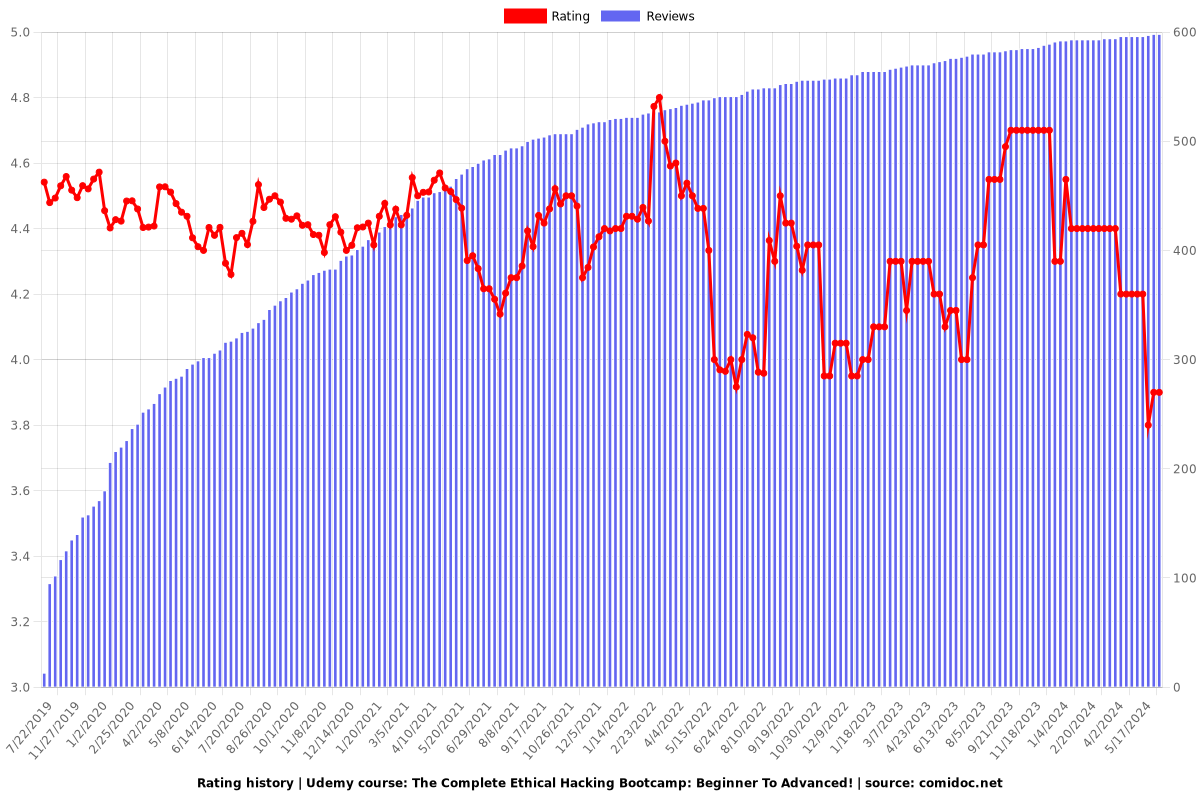
4.20 (596 reviews)

4,938
students
27.5 hours
content
Jun 2019
last update
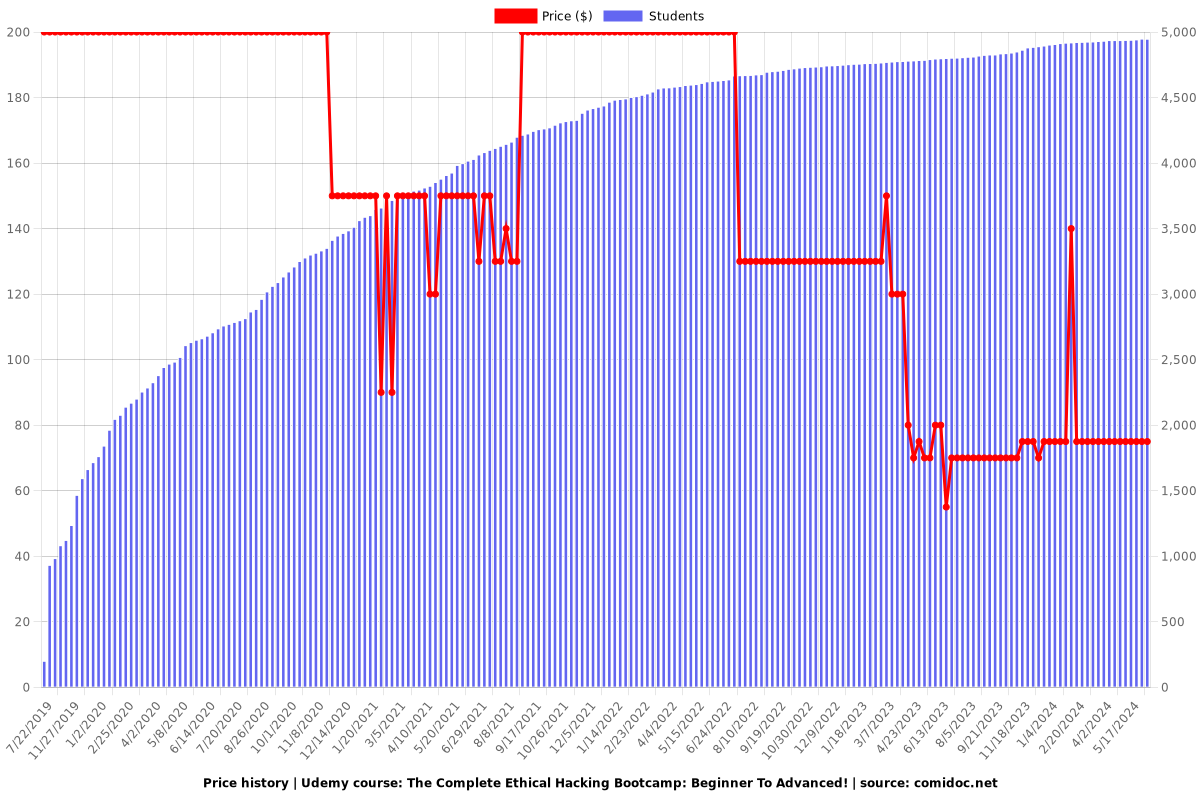
$74.99
regular price
What you will learn
How to setup a penetration testing environment.
How to use the Linux terminal.
Networking fundamentals
How to use networking tools
Passive information gathering
Google Dorks
Information Gathering With Shodan
Email Harvesting
DNS Enumeration and zone transfers
Active information gathering
Port scanning with Nmap
Using Nmap scripts
Web application penetration testing
HTTP requests and responses
Burpsuite fundamentals
Brute force attacks
Command Injection
SQL Injection
Cross Site Scripting (XSS)
Wireless penetration testing
Capture handshakes with Airodump-ng
Cracking passwords with Aircrack-ng
Generating wordlists with crunch
Rainbowtables
Arpspoofing
DNS spoofing
Exploiting browsers with BEEF
MITM Attacks
Metasploit
Msfconsole
Msfvenom
Command Injection
Meterpreter sessions
Python basics
Developing a custom backdooor
Developing a keylogger
Developing an offensive bruteforce script
Why take this course?
🚀 **The Complete Ethical Hacking Bootcamp: Beginner To Advanced!** 🛡️
---
### **Course Headline:**
Learn hands-on ethical hacking, penetration testing, web app pentesting and Python scripting.
---
### **Course Description:**
Dive deep into the world of cybersecurity with our comprehensive Ethical Hacking Bootcamp! This course is designed to take you from a complete beginner to an advanced penetration tester over 25 hours of video lectures. With a focus on practical, hands-on learning, you'll build your own Virtual Hacking Lab using VirtualBox and become proficient in Linux. You'll master network scanning and mapping with Nmap, learn the intricacies of exploitation with Metasploit, and understand how to securely crack Wi-Fi networks.
**What You'll Learn:**
- 🛠️ **Set Up Your Virtual Hacking Lab:** Get hands-on experience with setting up and managing your own lab environment.
- 🔧 **Linux Essentials:** Gain the essential skills needed to navigate and operate within Linux, a key component in ethical hacking.
- 🌍 **Networking Fundamentals:** Understand the basics of networking, including TCP/IP and the OSI model.
- 🕵️♂️ **Information Gathering:** Learn how to legally collect information on systems and networks to prepare for testing.
- ⚔️ **Exploitation & Privilege Escalation:** Discover how to identify vulnerabilities and exploit them, as well as escalate privileges with tools like Metasploit.
- 💻 **Web App Pentesting:** Explore the dark corners of web applications to find and exploit vulnerabilities such as SQL injection, XSS, CSRF, and command injection.
- ✈️ **Wireless Pentesting & Man in the Middle Attacks:** Learn to test wireless networks, crack WIFI passwords, and carry out man-in-the-middle attacks.
- 📚 **Offensive Python Scripting:** Develop your own penetration testing scripts and tools with Python, enhancing your hacking capabilities and automation skills.
---
### **Real Student Reviews & Testimonials:**
- 🚀 Excellent Explanations - Larry Bensky
"The explanation of what is being performed is spot on. Everything is explained and the pace is exactly as needed." - 🌟 Great course, lot's of quality content - Javier
"Great course. I got lots of quality content, where I have learned a lot. This course is great for beginners as it covers lots of topics in an easy manner. I loved developing the key-logger and the backdoor." - 👩💻 The instructor is very good - Davis Ansong
"The instructor is very good. The matched my expectations. Anyone wanting to get into IT and ethical hacking should have a look at this course." --- ### **Course Structure:** The course is carefully tailored to ensure a smooth learning curve, with each module building upon the previous one. Here's what you can expect: 1. 🏭 Setting up a penetration testing lab
Learn how to set up and manage your own virtual hacking lab to practice your skills in a controlled environment. 2. 🔧 Linux Essentials
Get familiarized with the Linux operating system and its most important commands, setting the foundation for your ethical hacking journey. 3. 🌐 Networking Fundamentals
Cover the basics of networking protocols and models to understand the infrastructure you'll be testing. 4. 🕵️♂️ Information Gathering
Master both passive and active information gathering techniques to prepare for your penetration tests. 5. 🚀 Exploitation & Privilege Escalation
Learn how to exploit systems using tools like Metasploit, and escalate privileges to understand the full scope of a system's vulnerabilities. 6. 💥 Web App Pentesting
Explore the common vulnerabilities found in web applications and how to exploit them effectively. 7. ✈️ Wireless Pentesting & Man in the Middle Attacks
Test wireless networks, intercept and analyze communication, and carry out man-in-the-middle attacks to secure and exploit wireless systems. 8. 👨💻 Offensive Python scripting
Learn the fundamentals of Python and how to develop your own offensive tools for penetration testing and automation tasks. --- Join us on this journey to master ethical hacking, penetration testing, and Python scripting. Elevate your cybersecurity skills and become an asset in protecting digital systems from malicious attacks. Enroll now and transform your career! 🔒🔥 --- **Note:** This course is designed for educational purposes only. Ethical hacking techniques should always be used responsibly and within the boundaries of the law. Always ensure you have permission before testing any system.
"The explanation of what is being performed is spot on. Everything is explained and the pace is exactly as needed." - 🌟 Great course, lot's of quality content - Javier
"Great course. I got lots of quality content, where I have learned a lot. This course is great for beginners as it covers lots of topics in an easy manner. I loved developing the key-logger and the backdoor." - 👩💻 The instructor is very good - Davis Ansong
"The instructor is very good. The matched my expectations. Anyone wanting to get into IT and ethical hacking should have a look at this course." --- ### **Course Structure:** The course is carefully tailored to ensure a smooth learning curve, with each module building upon the previous one. Here's what you can expect: 1. 🏭 Setting up a penetration testing lab
Learn how to set up and manage your own virtual hacking lab to practice your skills in a controlled environment. 2. 🔧 Linux Essentials
Get familiarized with the Linux operating system and its most important commands, setting the foundation for your ethical hacking journey. 3. 🌐 Networking Fundamentals
Cover the basics of networking protocols and models to understand the infrastructure you'll be testing. 4. 🕵️♂️ Information Gathering
Master both passive and active information gathering techniques to prepare for your penetration tests. 5. 🚀 Exploitation & Privilege Escalation
Learn how to exploit systems using tools like Metasploit, and escalate privileges to understand the full scope of a system's vulnerabilities. 6. 💥 Web App Pentesting
Explore the common vulnerabilities found in web applications and how to exploit them effectively. 7. ✈️ Wireless Pentesting & Man in the Middle Attacks
Test wireless networks, intercept and analyze communication, and carry out man-in-the-middle attacks to secure and exploit wireless systems. 8. 👨💻 Offensive Python scripting
Learn the fundamentals of Python and how to develop your own offensive tools for penetration testing and automation tasks. --- Join us on this journey to master ethical hacking, penetration testing, and Python scripting. Elevate your cybersecurity skills and become an asset in protecting digital systems from malicious attacks. Enroll now and transform your career! 🔒🔥 --- **Note:** This course is designed for educational purposes only. Ethical hacking techniques should always be used responsibly and within the boundaries of the law. Always ensure you have permission before testing any system.
Our review
🏆 **Global Course Rating:** 4.20
Based on the recent reviews, it's clear that the course strikes a balance between comprehensibility and technical depth. The majority of reviewers found the content informative and suitable for beginners looking to delve into ethical hacking and system administration. Here are the **Pros** and **Cons** based on the feedback:
### Pros:
- 🎓 **Comprehensive Content:** Reviewers appreciate the breadth of topics covered, from basic Linux system administration to more advanced hacking techniques.
- ✅ **Simplicity:** The course is commended for breaking down complex concepts into simpler terms, making it accessible to novices.
- 🛠️ **Practical Skills:** Students are able to learn by doing, with opportunities to practice real-world skills.
- 💼 **Relevance:** The course content is seen as relevant and beneficial for those aiming to pursue a career in cybersecurity or related fields.
- 👍 **Engaging Presentation:** The material is presented in a way that maintains the learners' interest and encourages continued study.
### Cons:
- 🎧 **Audio Issues:** Several reviewers noted audio quality issues that can make understanding content more challenging.
- ⏱️ **Technical Updates Needed:** Some of the downloadable files appear to be outdated, and there is a need for updates to reflect current tools and methods.
- 🔧 **Inconsistencies in Instructions:** There are instances where instructions provided in the videos may not lead to expected results due to changes in software or system configurations.
- ✏️ **Documentation Errors:** A few reviewers pointed out inaccuracies in some of the scripts or commands presented, which could mislead learners if not clarified.
- 🎬 **Video Quality:** Some videos lack clear visuals, making it hard to follow along without additional reference materials.
### Additional Notes:
- 🛠️ **Exploit Development Lecture:** There is a request for an additional lecture on exploit development to further enhance the course's completeness.
- 📚 **Resources Up-to-Date:** There are mentions of outdated download links, and it's recommended that the course content is updated to include the latest versions of tools like Kali Linux, which now comes in an `.ova` format for Virtualbox.
### Learner Feedback:
- 💖 **Appreciation for Effort:** Many reviewers expressed gratitude for the time and effort put into creating the course and accompanying materials.
- 📬 **Community Interaction:** The positive feedback on the creator's engagement with the community through replies to questions and the provision of YouTube content indicates a strong student-instructor relationship.
- 👀 **Eye on Offensive Hacking:** Some learners expressed interest in more offensive or advanced hacking courses, suggesting a demand for a broader spectrum of topics.
### Conclusion:
Overall, the course is highly regarded as valuable and educational content for beginners interested in cybersecurity. However, to improve, attention should be given to refining video and audio quality, updating resources, and ensuring that all instructions are accurate and up-to-date with current technologies. With these improvements, the course has the potential to be an even more effective learning tool.
Charts
Price
Rating
Enrollment distribution
Related Topics
2425814
udemy ID
6/23/2019
course created date
7/22/2019
course indexed date
Bot
course submited by