The Complete Penetration Testing Bootcamp
Learn Penetration Testing The Right Way! Learn All The Ethical Hacking & Penetration Testing Techniques Used By Hackers
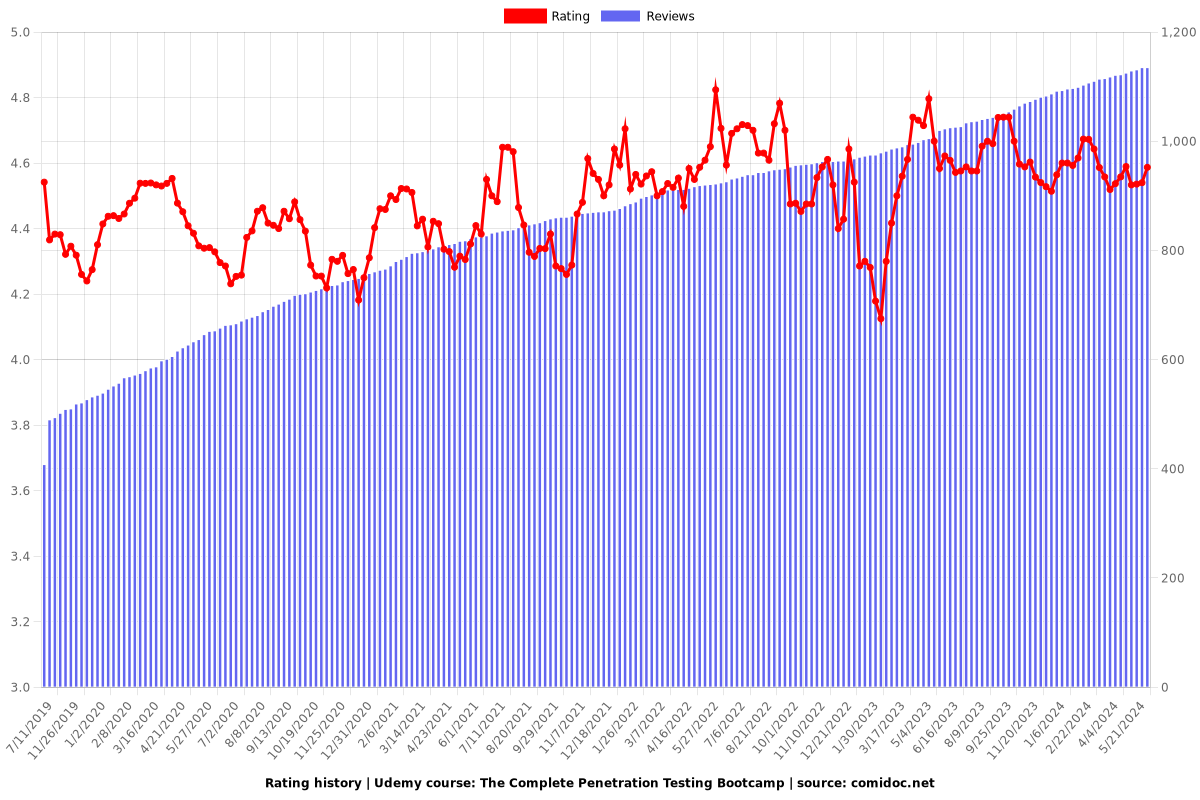
4.53 (1129 reviews)

18,972
students
10.5 hours
content
Oct 2018
last update
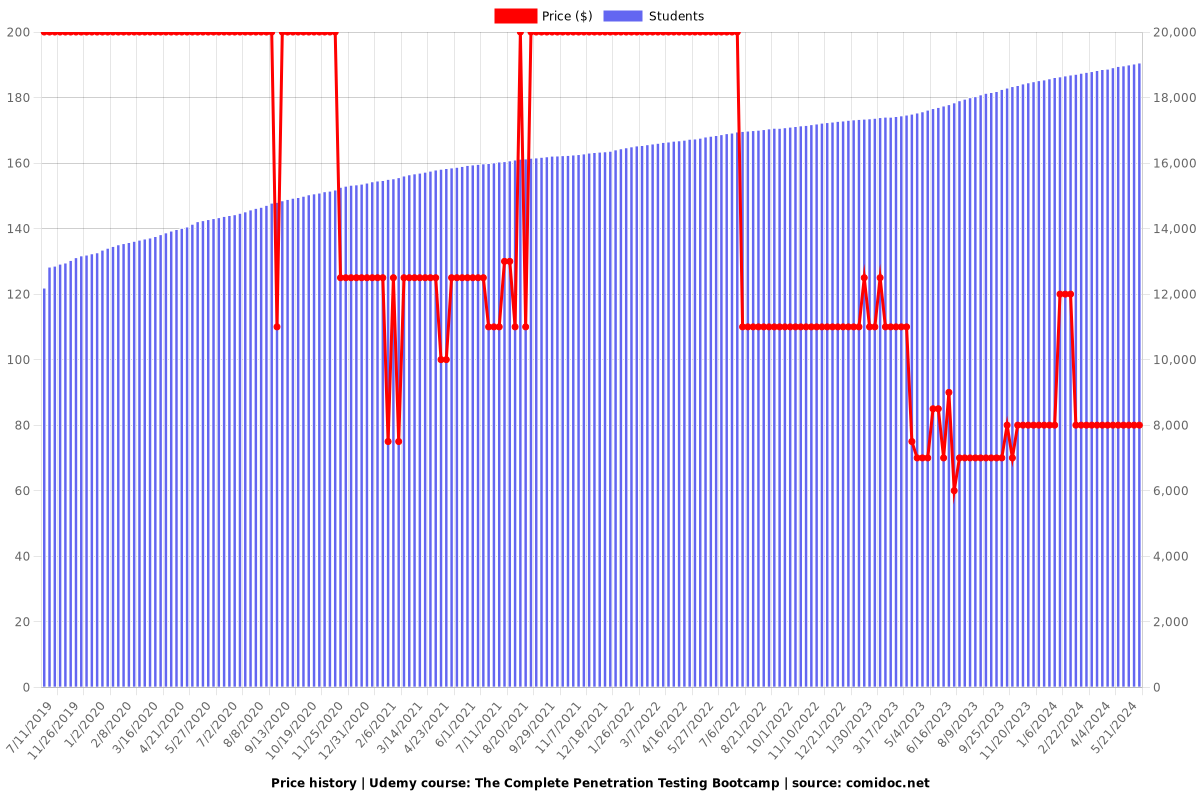
$79.99
regular price
What you will learn
Setup your own virtual penetration testing lab
Completely anonymize your online and hacking activity
Setup a VPN with Kali Linux
Setup Proxychains and a VPN for maximum anonymity and minimum DNS leaks
Use the Linux terminal for Ethical Hacking
Setup Terminal alternatives to boost productivity
Understand the networking fundamentals behind ethical hacking and penetration testing
Understand the OSI layer
Understand the 3 way TCP handshake
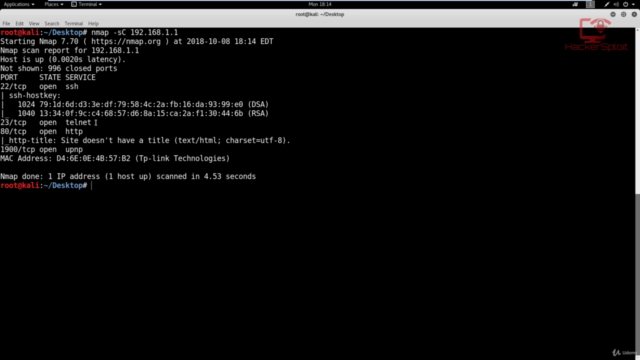
Grasp the usaage of Nmap for information gathering
Understand the Nmap syntax for a variety of scans
Use Nmap for advanced discovery
Use Nmap for advanced information gathering
Understand the Metasploit syntax for ethical hacking
Understand the Metasploit terminology used for penetration testing and ethical hacking
Perform exploitation with Metasploit
Install the Metasploit community Web GUI edition
Web server hacking with Metasploit
FTP Backdoor exploitation
Using Nikto Web vulnerability scanner
Wordpress hacking
Using WPScan
Password cracking with John The Ripper
BeEF browser exploitation
Bruteforce attacks
Arimtage
Using Veil Evasion
Generating Wordlists
Using Netcat
Arp spoofing
Arp poisoning
WPA/WPA2 cracking with aircrack-ng
WPA/WPA2 cracking with airgeddon
DDoS Attacks
Network sniffing with Wireshark
Meterpreter
Generating backdoors
Using RAT's
Why take this course?
🚀 **The Complete Penetration Testing Bootcamp: Learn All The Ethical Hacking & Penetration Testing Techniques!**
Are you ready to dive into the world of cybersecurity and master penetration testing? 🔒💻 With "The Complete Penetration Testing Bootcamp" by HackerSploit Academy, you'll embark on an educational adventure that transforms you from a novice to an advanced ethical hacker. This course is the ultimate support for the HackerSploit YouTube channel, where some of the content is available for free—and this course offers exclusive private videos that justify its existence. ✨
**Why Choose This Course?**
- **Comprehensive Curriculum**: This isn't just another course; it's a complete package designed to take you through every aspect of Ethical Hacking and Penetration Testing.
- **Beginner to Advanced**: Regardless of your current skill level, from beginner to advanced, this course will guide you on a journey of learning and mastery.
- **Support HackerSploit**: By purchasing this course, you directly support the HackerSploit YouTube channel, enabling them to continue providing valuable content.
**Course Highlights:**
- 🎬 **Essential Ethical Hacking Techniques**: Learn the best frameworks and techniques used by professional hackers ethically.
- 🧩 **Set Up Your Environment**: Understand how to set up a secure and safe penetration testing environment.
- 🛠️ **Linux Mastery for Hackers**: Get hands-on with Linux, the powerhouse operating system of choice for ethical hackers.
- 🌐 **Network Fundamentals**: Dive into networking fundamentals essential for any ethical hacker.
- 📊 **Information Gathering with Nmap**: Master the art of information gathering using tools like Nmap.
- 🔫 **Exploitation with Metasploit**: Learn to use Metasploit for penetration testing and ethical hacking, turning theory into practice.
- 🛢️ **Web Server Hacking**: Explore the dark corners of web server vulnerabilities and learn how to exploit them.
- 🚀 **Client & Server Side Exploitation**: Discover advanced client-side and server-side exploits that can compromise systems.
- 🔑 **Wireless Network Attacks (WPA/WPA2)**: Unlock the secrets of attacking wired and wireless networks for complete network domination.
- 📈 **Network Sniffing with Wireshark**: Learn to use Wireshark to analyze and sniff network traffic like a pro.
- 🕵️♂️ **Post Exploitation & Privilege Escalation**: Gain the skills needed to exploit vulnerabilities post-exploitation and escalate privileges.
**What Will You Learn?**
- Basic terminology and concepts in cybersecurity and ethical hacking.
- Setting up a secure environment for testing without compromising sensitive data or systems.
- Advanced techniques for exploitation, using frameworks like Metasploit to their fullest potential.
- How to use Linux effectively in the realm of ethical hacking.
- Networking basics that are crucial for understanding how to attack networks effectively.
- And much, much more! 📚💫
This course is tailored for anyone interested in cybersecurity, from those with no prior experience to seasoned professionals looking to refine their skills. Whether you're a complete beginner or have dabbled in hacking before, "The Complete Penetration Testing Bootcamp" provides all the knowledge and practical skills you'll ever need to become an ethical hacker. 🎖️
Don't miss out on this opportunity to join the ranks of cybersecurity experts! Enroll now and start your journey into the fascinating and challenging world of ethical hacking and penetration testing with HackerSploit Academy. 🌐💪
Screenshots
Our review
Based on the recent reviews for the course "Ethical Hacking from Scratch," here is a synthesized review:
### Course Overview:
The course "Ethical Hacking from Scratch" has received a global rating of 4.54, indicating that most students have had a positive experience with the content and delivery. The course seems to cater to individuals with a foundational understanding of computer systems, as well as those looking for advanced knowledge on topics such as SQL injections and exploits.
### Pros:
- **Comprehensive Content:** The course covers a wide range of ethical hacking concepts, making it informative for self-study, especially for beginners in penetration testing. (Multiple reviews)
- **Clear Explanations:** The instructor is commended for their thorough explanations of intricate concepts, which are presented in an engaging manner. (Several reviews)
- **Real-World Application:** The course content is described as realistic and practical, with the instructor's passion for the subject evident in the lessons. (Several reviews)
- **Quality Production:** Videos and sound quality are reported to be of good quality, contributing to an enhanced learning experience. (Multiple reviews)
- **Responsive Instructor:** The instructor is known for being responsive in Q&A, which adds value to the course. (Several reviews)
- **Experienced Instructor:** The instructor has a strong background, which is beneficial for students looking to learn from someone with real-world experience. (Multiple reviews)
- **Engaging Delivery:** The instructor's engaging delivery and clear objectives make the course appealing and easy to follow. (Several reviews)
- **Hands-On Approach:** The course is praised for showing how to perform tasks instead of just explaining them, allowing learners to apply what they've learned directly. (Several reviews)
- **Advanced Content:** For more experienced individuals, the course offers advanced cybersecurity content that is described as the best at an advanced level. (Multiple reviews)
- **Long-Term Learning Resource:** The course content has been a main source of learning for some students over several years, indicating its enduring value. (Several reviews)
### Cons:
- **Prior Technical Knowledge Required:** Some reviewers suggest that the course is best suited for individuals who have significant technical knowledge, particularly in networking and Linux command line proficiency. (Several reviews)
- **Not Suitable for Complete Beginners:** The content may be overwhelming or not appropriate for complete beginners without a technical background. (Multiple reviews)
- **Tooling Expectations:** There is feedback indicating that the course assumes familiarity with certain tools that might not be covered in the early stages of the course. (Several reviews)
- **Misalignment with Advertised Level:** A few reviewers experienced a mismatch between their expected learning level and the course's actual difficulty, which could lead to frustration if the student is not at the intermediate level or above. (Few reviews)
### Recommendations from Learners:
- **Pre-requisites Clarification:** It is recommended that students review the course prerequisites carefully and ensure they have the necessary technical foundations before enrolling.
- **Advanced Content Expansion:** Some learners suggest adding advanced topics such as hardware hacking or SCADA/ICS systems. (Several reviews)
- **Course Updates:** Learners appreciate it when courses are kept up to date with the latest techniques and tools, so consistent updates are encouraged. (Multiple reviews)
### Final Thoughts:
"Ethical Hacking from Scratch" is a well-regarded course that provides substantial content for those looking to dive into the world of penetration testing or cybersecurity. It is particularly beneficial for those with prior technical knowledge and experience. The course's strength lies in its detailed explanations, hands-on demonstrations, and clear delivery by an experienced instructor. Potential students should consider their current technical expertise before enrolling to ensure the course aligns with their learning objectives and level of proficiency. Overall, the course has proven to be a valuable resource for many learners and continues to receive support and appreciation from its student base.
Charts
Price
Rating
Enrollment distribution
Related Topics
1687478
udemy ID
5/11/2018
course created date
7/11/2019
course indexed date
Bot
course submited by