Ultimate Ethical Hacking from Zero To Hero
Become an ethical hacker that can hack computer systems like black hat hackers and secure them like security experts.

What you will learn
Ethical Hacking Essentials
The Ethical Hacking Process
Linux Basics
Web App Basics
Networking Essentials + Wireshark
Nmap Port Scanner
Python Basics
Black Hat Techniques
Mr Robot TV Show in Real life
Why take this course?
What is Ethical Hacking?
Ethical hacking is an authorized practice of detecting vulnerabilities in an application, system, or organization’s infrastructure and bypassing system security to identify potential data breaches and threats in a network. Ethical hackers aim to investigate the system or network for weak points that malicious hackers can exploit or destroy. They can improve the security footprint to withstand attacks better or divert them.
The company that owns the system or network allows Cyber Security engineers to perform such activities in order to test the system’s defenses. Thus, unlike malicious hacking, this process is planned, approved, and more importantly, legal.
Ethical hackers aim to investigate the system or network for weak points that malicious hackers can exploit or destroy. They collect and analyze the information to figure out ways to strengthen the security of the system/network/applications. By doing so, they can improve the security footprint so that it can better withstand attacks or divert them.
Ethical hackers are hired by organizations to look into the vulnerabilities of their systems and networks and develop solutions to prevent data breaches. Consider it a high-tech permutation of the old saying “It takes a thief to catch a thief.”
They check for key vulnerabilities include but are not limited to:
Injection attacks
Changes in security settings
Exposure of sensitive data
Breach in authentication protocols
Components used in the system or network that may be used as access points
Reviews
Charts
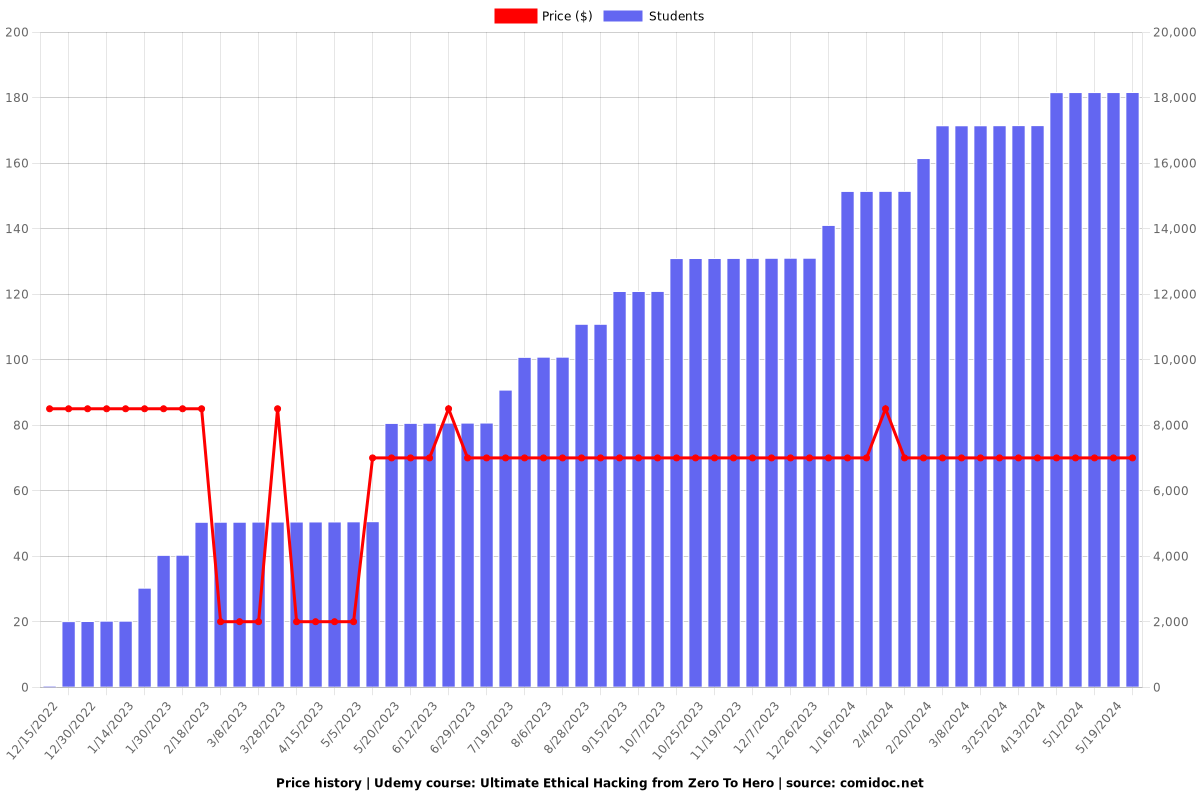
Price
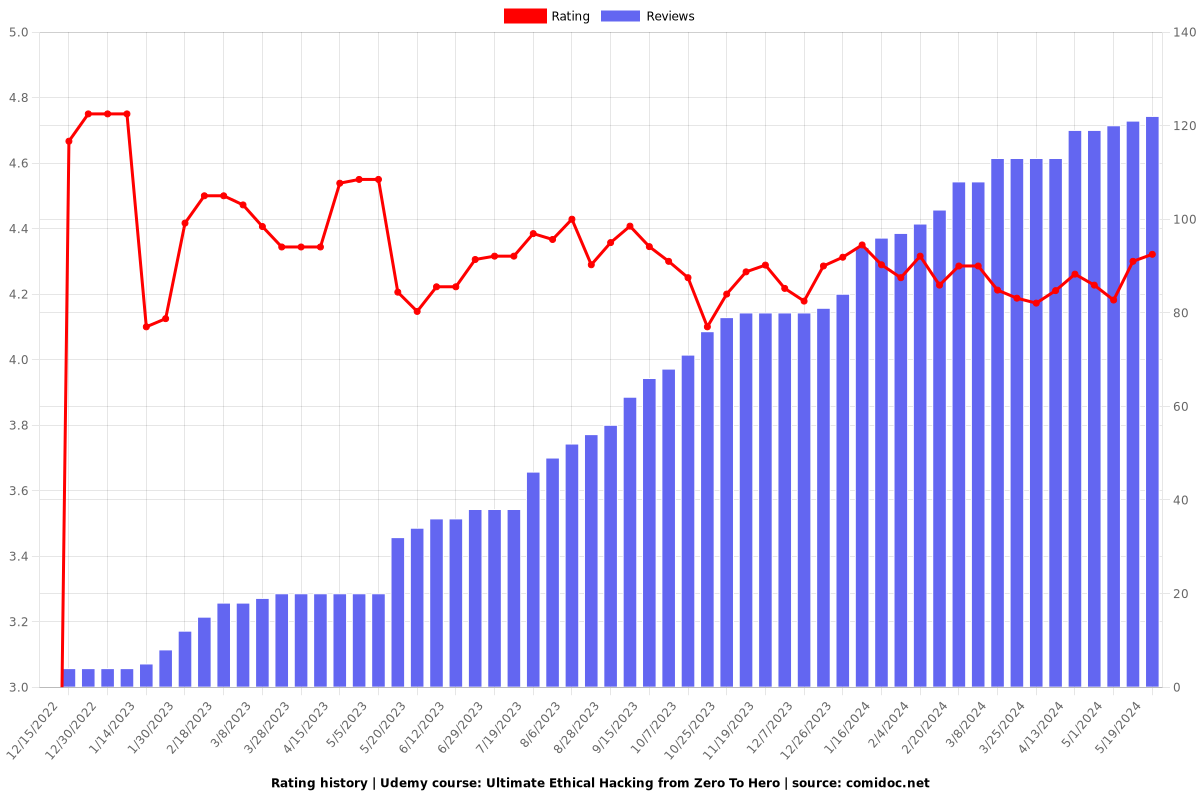
Rating
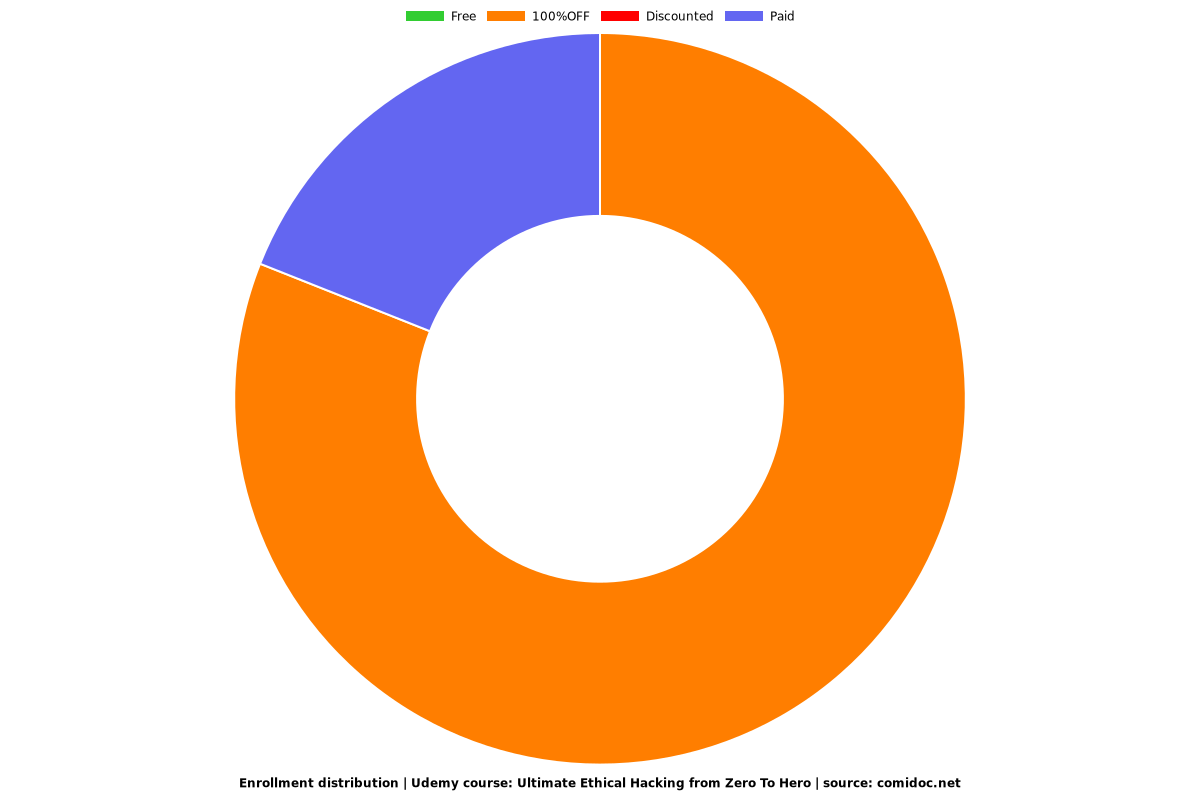
Enrollment distribution